SSO
Enable or disable Single Sign-On (SSO) for secure authentication across SearchBlox Admin Console
Single Sign-On (SSO) is a powerful authentication method that simplifies user access to multiple applications and websites by allowing them to log in with a single set of credentials. In the context of SearchBlox, SSO can be enabled or disabled for the Admin Console, providing flexibility and enhanced security for administrators.
Key Features of SSO in SearchBlox
- Simplified Access:
Users can log in to the SearchBlox Admin Console using their existing SSO credentials (e.g., from Google, Microsoft, or other identity providers).
Eliminates the need to remember multiple usernames and passwords. - Enhanced Security:
SSO relies on trusted identity providers, reducing the risk of weak or reused passwords.
Centralized authentication makes it easier to enforce security policies (e.g., multi-factor authentication). - Flexibility:
SSO can be enabled or disabled based on organizational requirements.
Works with popular identity providers that support standard protocols like SAML or OAuth. - Seamless Integration:
Integrates with existing enterprise identity management systems, ensuring a smooth user experience.
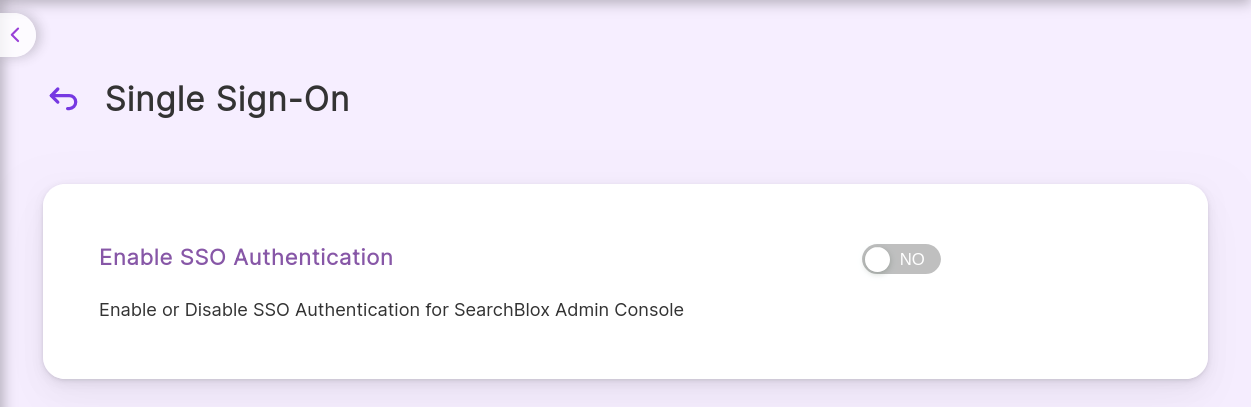
Enable SSO Authentication
- Access Admin Console:
Log in to the SearchBlox Admin Console with administrator privileges. - Navigate to SSO Settings:
Go to the Security or Authentication section in the Admin Console. - Toggle the SSO option to Enable.
To enable SSO Authentication in SearchBlox, SAML Configuration is required. The following table outlines the fields and their descriptions for configuring SAML-based SSO:
| Field | Description |
|---|---|
| SearchBlox URL | This is the base URL used to generate the SearchBlox Service Provider(SP) Metadata file for SSO. URL Format Example: <Host/Domain Name>: port, <IP Address>: port. |
| IdP Metadata XML File | Upload the Identity Provider (IdP) Metadata XML File for SAML SSO. This file contains the IdP's configuration details, such as endpoints and certificates. |
| SP Metadata XML File | Download the SP Metadata XML File. This is a one time UI option provided immediately after uploading the IdP metadata XML file and Save the SAML configuration. You can also view the SP Metadata file information using https://localhost:8443/meta-saml |
| Entity ID | If the EntityID is configured, its value will be added to the Service Provider metadata file. Otherwise, the default ACS URL will be taken. Example URL: https://<ip/domain>/saml/callback?client_name=SAML2Client |
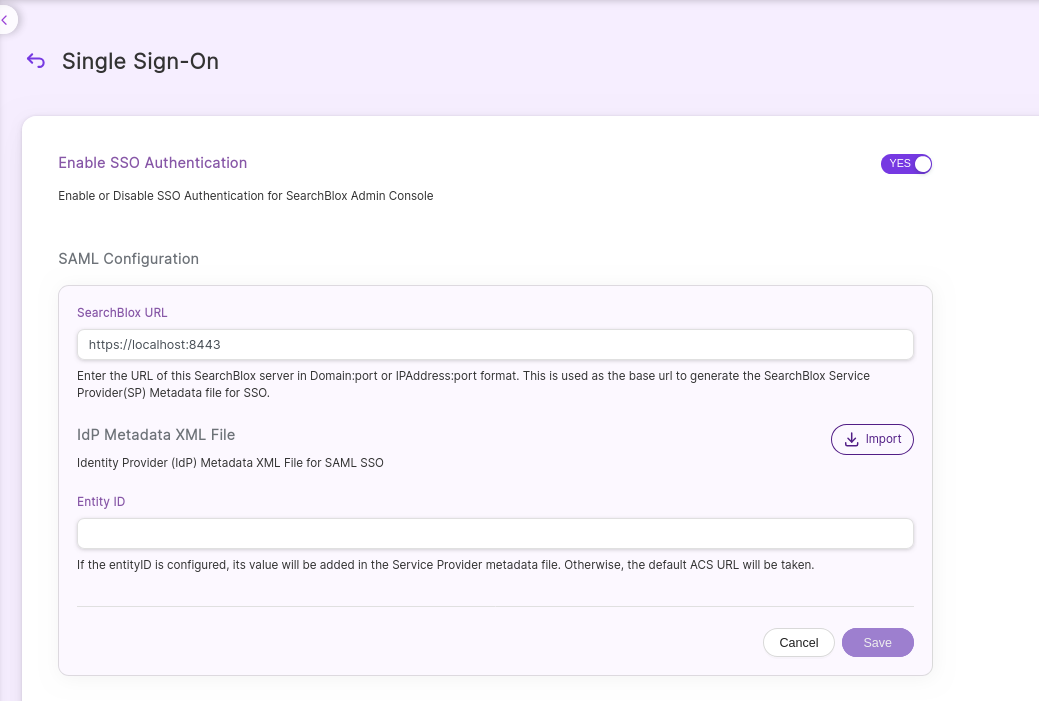
Notes:
- Upload IdP Metadata XML File:
Log in to the SearchBlox Admin Console.
Navigate to the SSO Settings or Authentication section.
Upload the IdP Metadata XML File provided by your Identity Provider (e.g., Azure AD, Okta, Google).- Restart SearchBlox:
After uploading the IdP Metadata XML file, restart the SearchBlox service to apply the changes.
This step is crucial for generating the SP Metadata file.- Locate the SP Metadata File:
Once SearchBlox has restarted, locate the SP Metadata file (sp-metadata.xml) in the following directory:
<SearchBlox-Installation-Directory>
This file contains the Service Provider (SP) configuration details required by your Identity Provider.- Upload SP Metadata File to IdP:
Download the sp-metadata.xml file from the SearchBlox installation directory.
Upload this file to your Identity Provider's configuration portal to complete the SSO setup.- Re-login to SearchBlox:
After uploading the SP Metadata file to your IdP, re-login to the SearchBlox Admin Console.
Use your SSO credentials to authenticate.- Use a Private Browser Window:
To avoid caching issues, perform the re-login in a private or incognito browser window.
This ensures that any cached credentials or sessions do not interfere with the SSO authentication process
Example Configuration
SearchBlox URL: https://searchblox.example.com:8443
IdP Metadata XML File: Upload the file provided by your Identity Provider (e.g., Azure AD).
SP Metadata XML File: Download and share this file with your Identity Provider.
Entity ID: https://searchblox.example.com/saml/callback?client_name=SAML2Client
SSO Authorized Users
To enable SSO authentication in SearchBlox, users must be added to both the Identity Provider (IdP) and the SearchBlox Realm. Only users added to the SearchBlox Realm are considered SSO authorized users and can access the system using SSO credentials.
Steps to Add and Manage SSO Authorized Users
- Add Users to Identity Provider (IdP):
Ensure that the users are added and configured in your Identity Provider (IdP) (e.g., Azure AD, Okta, Google).
The IdP will handle the authentication process and pass the user credentials to SearchBlox. - Add Users to SearchBlox Realm:
Log in to the SearchBlox Admin Console with administrator privileges.
Navigate to the SSO Authorized Users section (as shown in the screenshot).
Click the Add User button or link to add new users to the SearchBlox Realm. Provide the necessary user details, such as:- Username: Must match the username in the IdP.
- Email: User's email address.
- Roles: Assign appropriate roles (e.g., Admin, User) to define access permissions.
- Filter Users:
Use the filter option located at the top right corner of the SSO Authorized Users page to search for specific users.
Filters can be applied based on username, email, or roles. - Manage Users:
Edit User Details: Update user information, such as email or roles, as needed.
Delete Users: Remove users who no longer require access to SearchBlox.
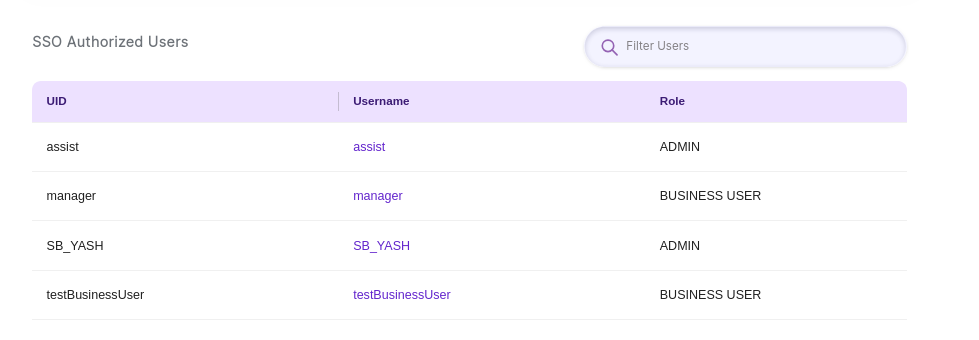
Key Points to Remember
- User Synchronization: Users must exist in both the IdP and the SearchBlox Realm to authenticate via SSO.
- Role Assignment: Assign appropriate roles to users in the SearchBlox Realm to control their access levels.
- Filtering: Use the filter option to quickly locate and manage users in large lists.
CAUTION
When you disable SSO, existing SAML configuration will be cleared. If you want to re-enable SSO, all the settings have to be configured again.
Updated 12 months ago
