LDAP/AD Realm
Secure Search can be enabled using LDAP/Active Directory by selecting the LDAP/AD Realm checkbox and entering all the required settings, as shown in the interface.
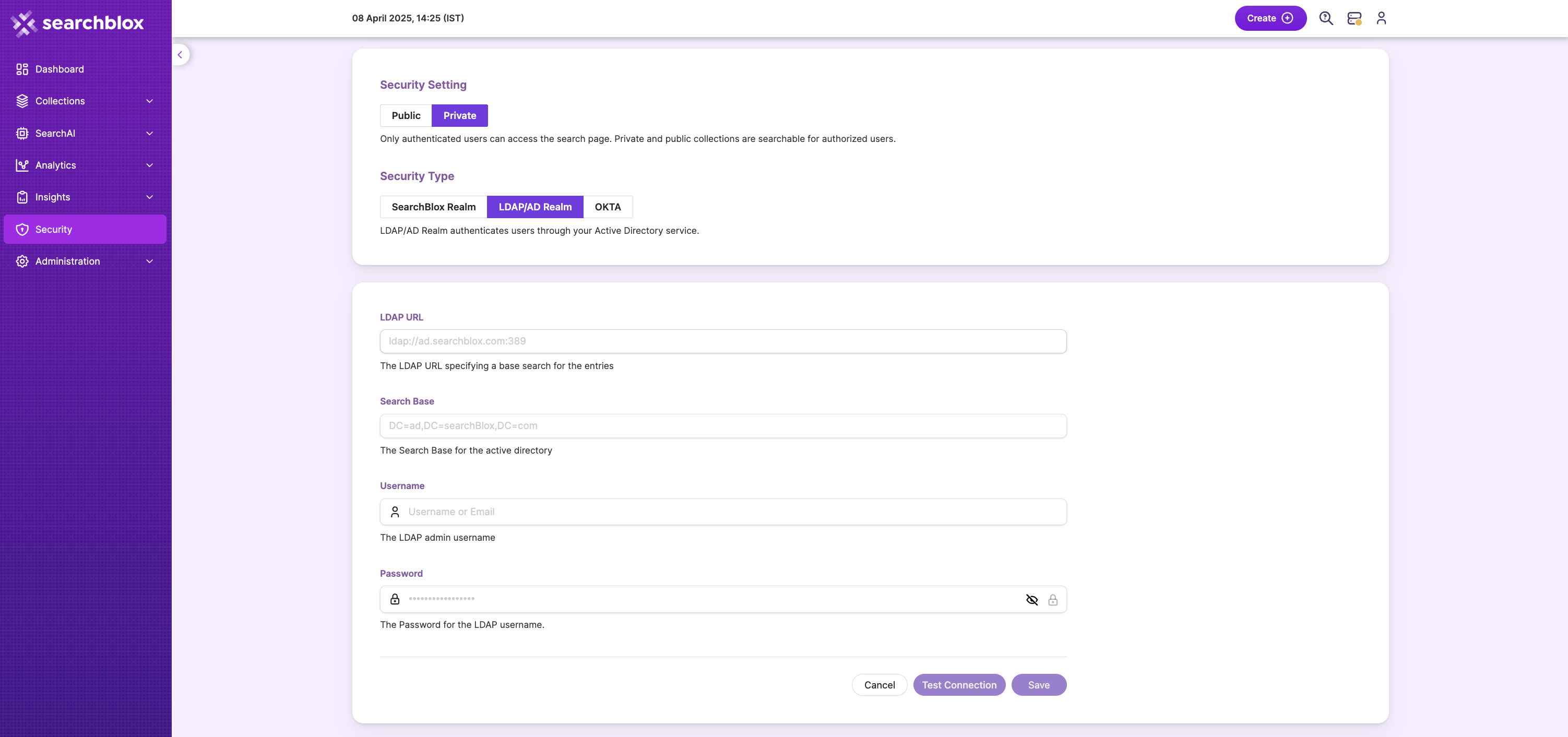
LDAP Settings
- Select LDAP/AD Realm
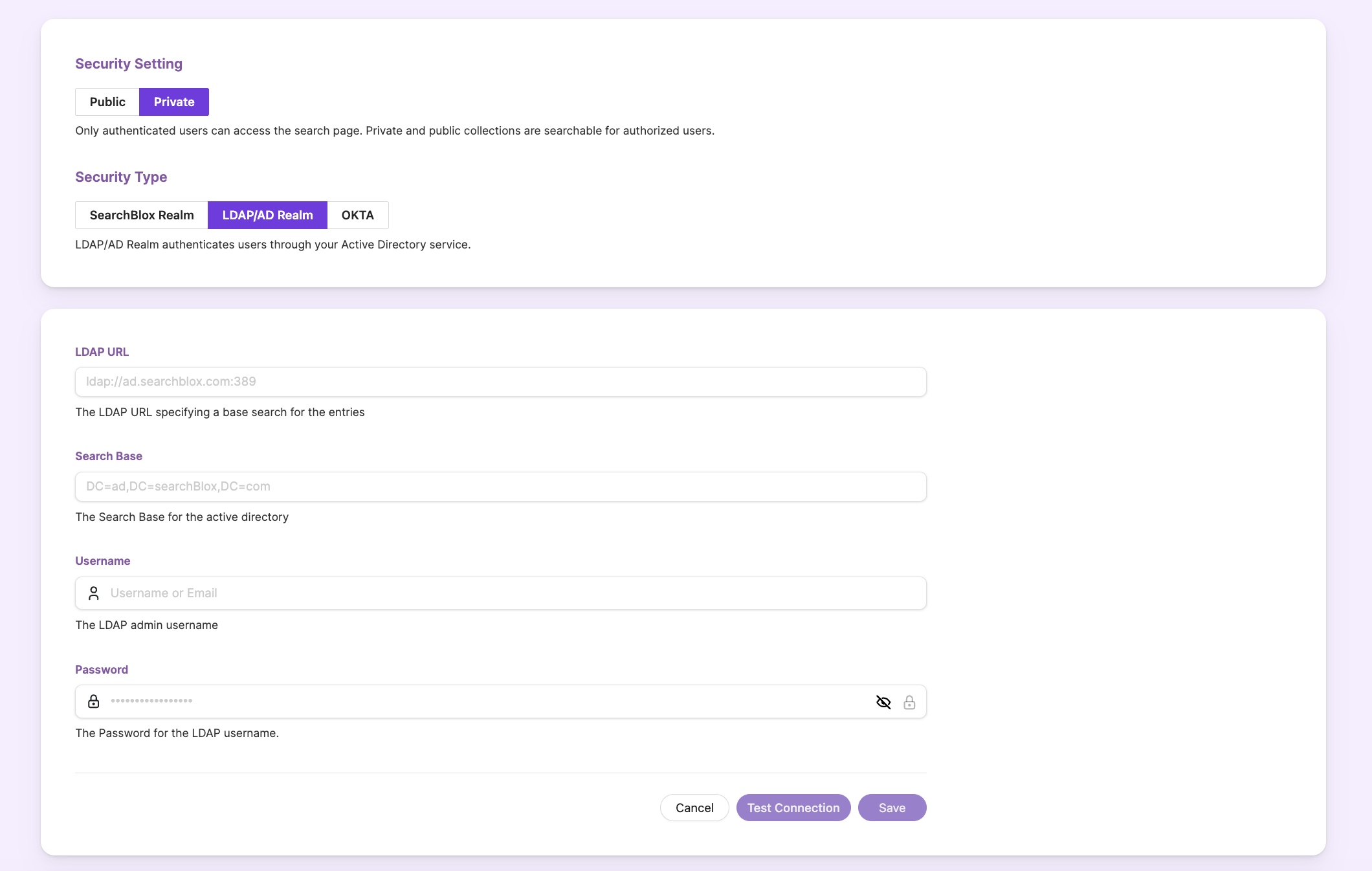
- Give the required LDAP details
| Field | Description |
|---|---|
| LDAP URL | The LDAP link that defines where the directory search should start. |
| Search Base | The main location in the Active Directory where the search begins. |
| Username | The admin username used to connect to LDAP/AD. |
| Password | The password for the admin username. |
- Test the connection. When the connection is successful, you will see a confirmation message as shown.
Add Security Group
- Using this setting you can configure security group settings for LDAP/ Active Directory.
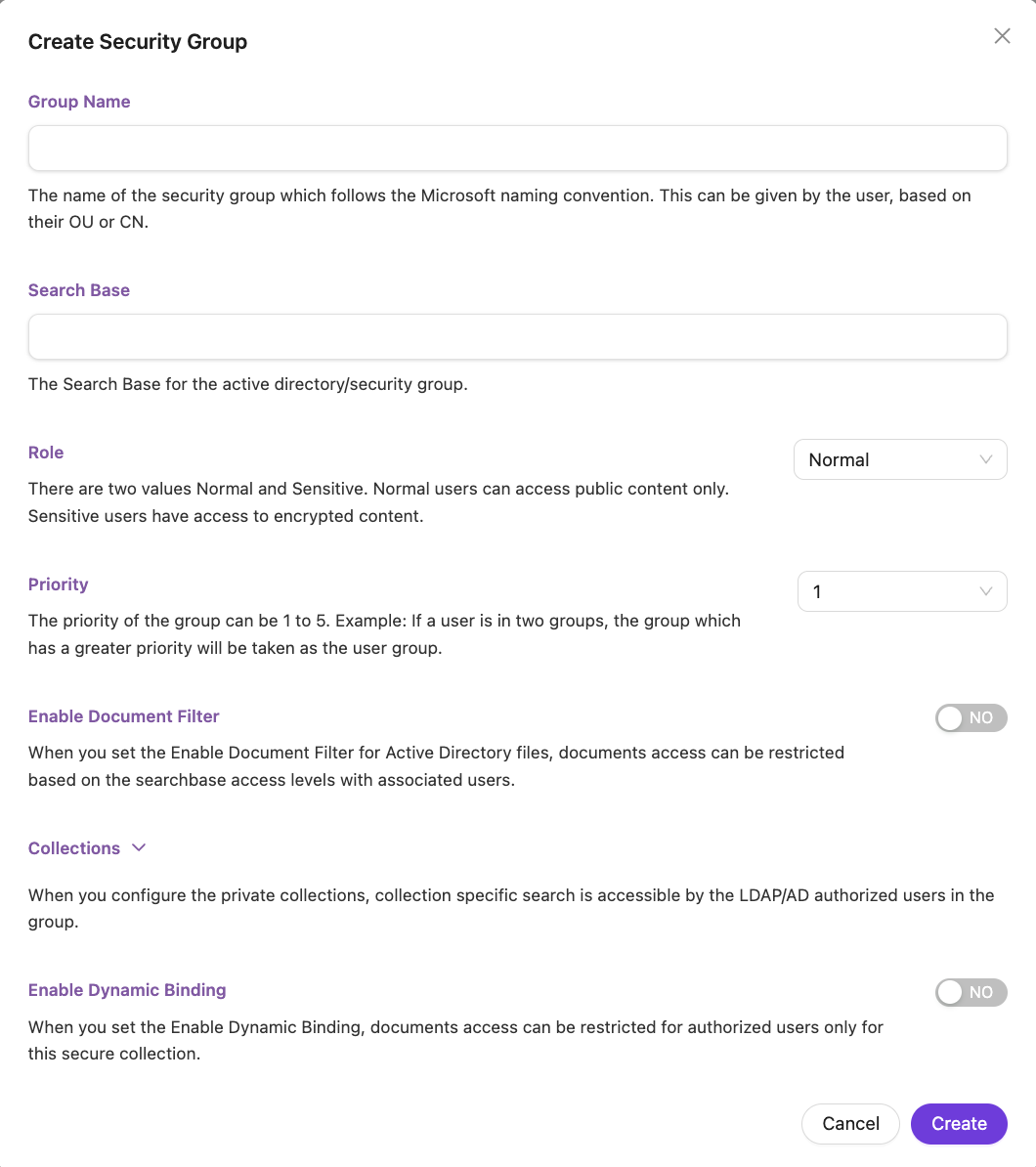
- Give the parameters for the Security Group for LDAP. The information on the parameters is provided in the following table
| Field | Description |
|---|---|
| Group Name | This is the name of the security group. You can choose any name based on your organizational unit (OU) or your needs. The name must be 3–50 characters long and can contain letters, numbers, and only one special character: the underscore ( _ ). |
| Search Base | Search Base for the active directory/security group |
| Role | There are two values Normal or Sensitive. Default is Normal. Sensitive users have access to encrypted content )Collection Encryption |
| Priority | This shows how important the group is. If a user belongs to two groups, the group with the higher priority number will be used for that user. |
| Collections | These are the collections that users in this group are allowed to access. |
- After you add the groups, you can see them listed on the Security User Groups dashboard, as shown
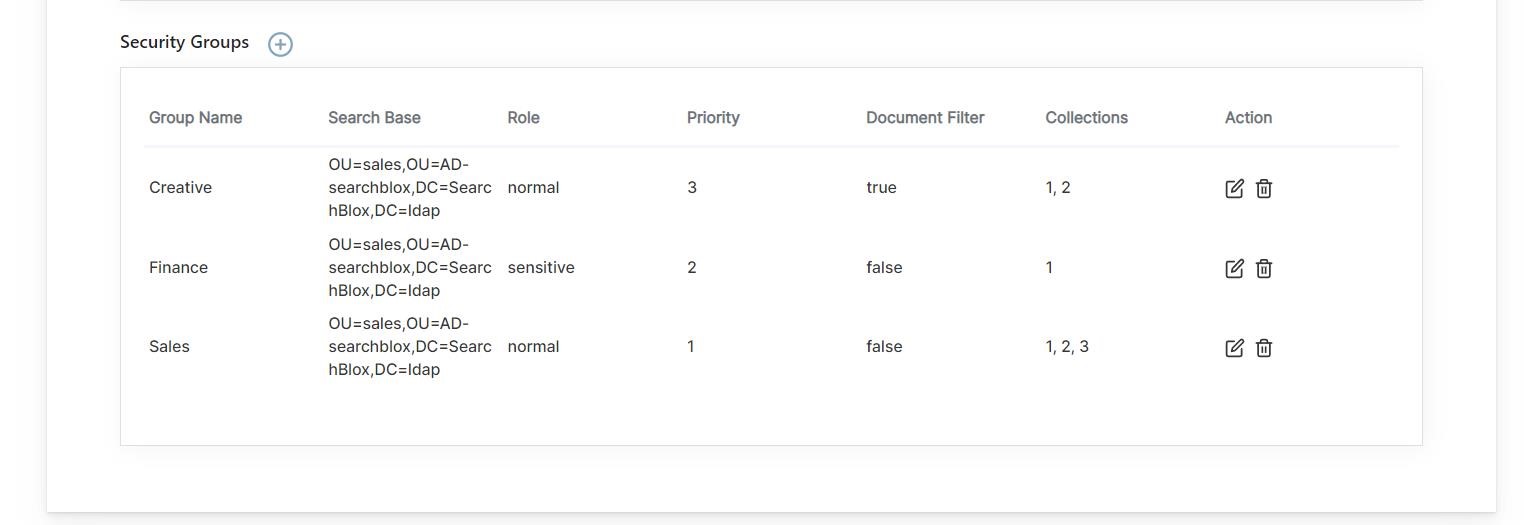
Features of Security Groups in LDAP Realm
Group Settings
- After you enter the LDAP settings, you must also add the Group settings.
These settings are needed to link collection-based security with LDAP security for search results. - When you create a group, you can choose a list of collections for that group.
A user who belongs to that group will be able to access only those assigned collections. - The users who belong to a specific Organizational Unit (OU) in LDAP will be placed inside the corresponding group in SearchBlox.
- You can create multiple groups for the same Organizational Unit (OU).
- The permissions and users for a group are taken based on the Search Base you provide. Because of this, the Search Base is an important value when creating Security User Groups.
Group Naming
- LDAP security groups can be named using Microsoft’s naming rules, and they may include special characters.
- According to the Microsoft documentation, the LDAP distinguished name is globally unique. For example, the distinguished name of a computer named mycomputer in the MyOrganizationalUnit organizational unit in the microsoft.com domain is CN=mycomputer, OU=MyOrganizationalUnit, DC=microsoft, DC=com.
- For example, “A602-AC-DMASFS2_sdata RW”
Priority
- When a user belongs to two groups, the group with the higher priority number will be chosen for that user.
For example:
If a user is in Group A with priority 5 (and has access to collection 1) and also in Group B with priority 3 (and has access to collection 2), the system will choose Group A because it has the higher priority.
So the user will only see results from collection 1.
Sensitive User
- Only the users with a sensitive role would be able to view encrypted content. Please refer Collection Encryption for more details on Encryption.
Accessing Secure Search for LDAP Realm
Log in using LDAP/AD credentials here:
https://localhost:8443/search/index.html
Then perform the secure search.
Updated 3 months ago
What’s Next
