SSL Configuration
SearchBlox server runs on SSL by default using a Self Signed Certificate. However as a good practice, we recommend you to add a valid SSL certificate to your domain using any hosting provider service or standard ways like Java Key Tool if you have the certificate ready.
Importing External SSL Certificate using Java Key Tool
Important Notes:
- When creating or exporting the JKS, be sure to specify format PKCS #12 and not JKS format. Jetty requires PKCS #12.
- If working with a SearchBlox cluster, specify all of the hostnames in the cluster as Subject Alt Names on the certificate. This lets you use the same certificate/JKS file for all machines in the cluster.
- While generating the certificate, please use the same password for all the commands to avoid confusion.
Follow the steps to import external SSL Certificates (.pem or .certs):
Step 1
Go to the path:
For Windows: C:\SearchBloxServer\etc
For Linux: /opt/searchblox/etc/
Note
If a keystore file is already present, you can either rename it or delete by taking a backup of it. If the cert file is of PKCS#7 format please skip step 2, 3 & 4 and continue from Step 4 Alternative.
Step 2
Generate a Java keystore and key pair
we need to create a .jks file (Example: searchblox.jks) using the following command .
keytool -genkey -alias searchblox -keyalg RSA -keystore searchblox.jks -keysize 2048
Step 3
Import a root or intermediate CA certificate to an existing Java keystore
If we have .pem/.cert (Example:searchblox.pem/searchblox.crt)
we need to import into searchblox.jks file which we have created in the previous step.
keytool -import -trustcacerts -alias sbx -file searchblox.pem -keystore searchblox.jks
Step 4
Converting the .JKS file into .P12 or .PKCS12 Format
In this step, we need to convert the searchblox.jks into searchblox.p12/searchblox.pkcs12 format.
keytool -importkeystore -srckeystore searchblox.jks -destkeystore searchblox.p12 -deststoretype PKCS12
Step 4 Alternative
Note: If the cert file is of PKCS #7 format, the above command (Step 4 command will throw an error) will not work. In this case, you can skip 2, 3 & 4 steps and run the below command for step 4 as an alternative. First PKCS #7 cert file has to be converted to .P12 or .PKCS12 Format using the below command:
openssl pkcs12 -export -in <searchblox.crt> -inkey <domain>.com.key -certfile <certificate-chain.crt> -out searchblox.p12
It will ask you to create a new password for PKCS12 file and ask for other required details(First name/last name is the CN (i.e must match FQDN that users will browse to)). Once you enter please type yes.
Step 5
Run the following command to create keystore file using PKCS12 file.
keytool -importkeystore -srckeystore searchblox.p12 -srcstoretype PKCS12 -destkeystore keystore
Step 6
Generating the OBF key
For Linux:
java -cp /opt/searchblox/lib/logging/slf4j-api-2.0.13.jar:/opt/searchblox/lib/logging/jetty-slf4j-impl-11.0.25.jar:/opt/searchblox/lib/jetty-util-11.0.25.jar org.eclipse.jetty.util.security.Password admin@1234
For Windows:
java -cp C:\SearchBloxServer\lib\logging\slf4j-api-2.0.13.jar;C:\SearchBloxServer\lib\logging\jetty-slf4j-impl-11.0.25.jar;C:\SearchBloxServer\lib\jetty-util-11.0.25.jar org.eclipse.jetty.util.security.Password Admin@123
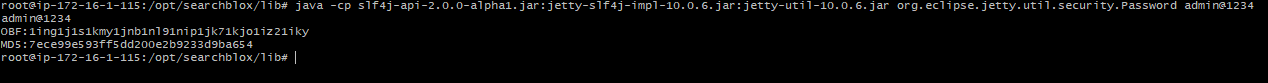
Step 7
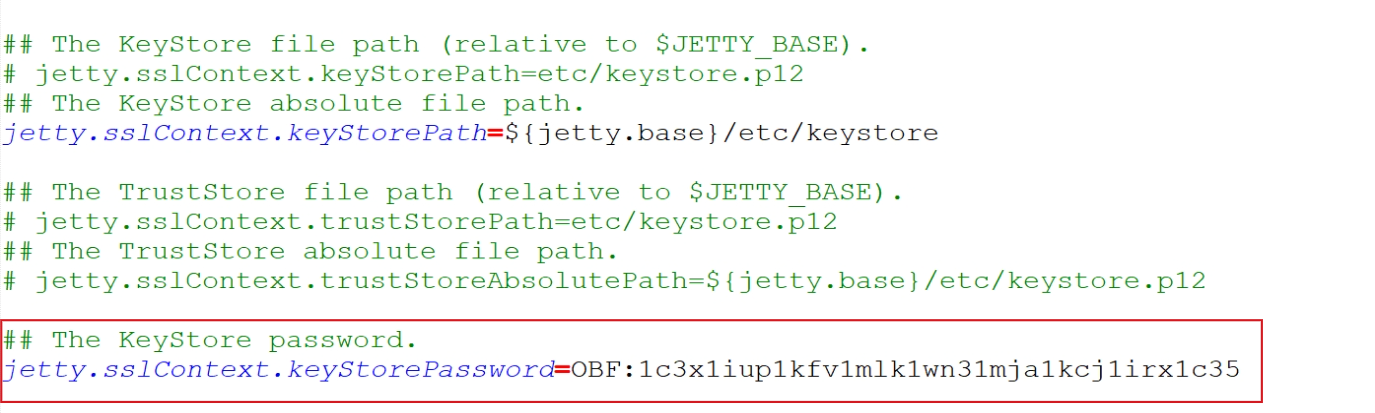
we have to update the OBF key value in to /opt/searchblox/start.d/ssl.ini
The KeyStore password:
jetty.sslContext.keyStorePassword=OBF:1ing1j1s1kmy1jnb1nl91nip1jk71kjo1iz21iky
Step 8
Stop and Start SearchBlox service
Open your browser and go to the URL: https://localhost:8443/console and confirm the valid SSL cert is now displayed when you click on the browsers lock icon.
Disable TLS
TLS can be disabled by updating the configuration within ../etc/jetty-ssl-context.xml
By default, only TLS v1.2 / TLS v1.3 is enabled. In case, If you see TLS v1 and TLS v1.1 are enabled, you can follow below steps to disable vulnerable TLS protocols.
Disable TLSv1 and TLSv1.1 using the steps below:
1.) Edit the following file after stopping SearchBlox service:
/opt/searchblox/etc/jetty-ssl-context.xml
or
C:\SearchBloxServer\etc\jetty-ssl-context.xml
2.) Add or update the required protocols under the sslContextFactory tag.
<Call name="setExcludeProtocols">
<Arg>
<Array type="String">
<Item>TLSv1</Item>
<Item>TLSv1.1</Item>
</Array>
</Arg>
</Call>
<Call name="addExcludeCipherSuites">
<Arg>
<Array type="String">
<Item>.*NULL.*</Item>
<Item>.*RC4.*</Item>
<Item>.*MD5.*</Item>
<Item>.*3DES.*</Item>
<Item>.*DES.*</Item>
<Item>.*DSS.*</Item>
</Array>
</Arg>
</Call>
3.) Restart the SearchBlox service.
Cipher suites in SSL
Cipher suites can be included or excluded by editing the the file ../etc/jetty-ssl-context.xml
To exclude cipher suites:
<Set name="ExcludeCipherSuites">
<Array type="String">
<Item>SSL_RSA_WITH_DES_CBC_SHA</Item>
<Item>SSL_DHE_RSA_WITH_DES_CBC_SHA</Item>
<Item>SSL_DHE_DSS_WITH_DES_CBC_SHA</Item>
<Item>TLS_DHE_RSA.*</Item>
<Item>TLS_ECDHE.*</Item>
</Array>
</Set>
To include cipher suites:
<Set name="IncludeCipherSuites">
<Array type="String">
<Item>SSL_RSA_WITH_DES_CBC_SHA</Item>
<Item>SSL_DHE_RSA_WITH_DES_CBC_SHA</Item>
<Item>SSL_DHE_DSS_WITH_DES_CBC_SHA</Item>
<Item>TLS_DHE_RSA.*</Item>
<Item>TLS_ECDHE.*</Item>
</Array>
</Set>
Disable SSL
- Go to <SEARCHBLOX_INSTALLATION_PATH>/start.d/http.ini and uncomment the following line
--module=http - Disable or comment the line
--module=httpsfrom file<SEARCHBLOX_INSTALLATION_PATH>/start.d/https.ini - Disable or comment the line
--module=sslfrom file<SEARCHBLOX_INSTALLATION_PATH>/start.d/ssl.ini - Restart SearchBlox
SearchBlox will be accessible only at http://localhost:8080/console
Updated 8 months ago
