LDAP/AD Realm
Secure Search can be used based on the LDAP/Active Directory configuration by enabling the checkbox LDAP/AD Realm and providing the required settings, as shown:
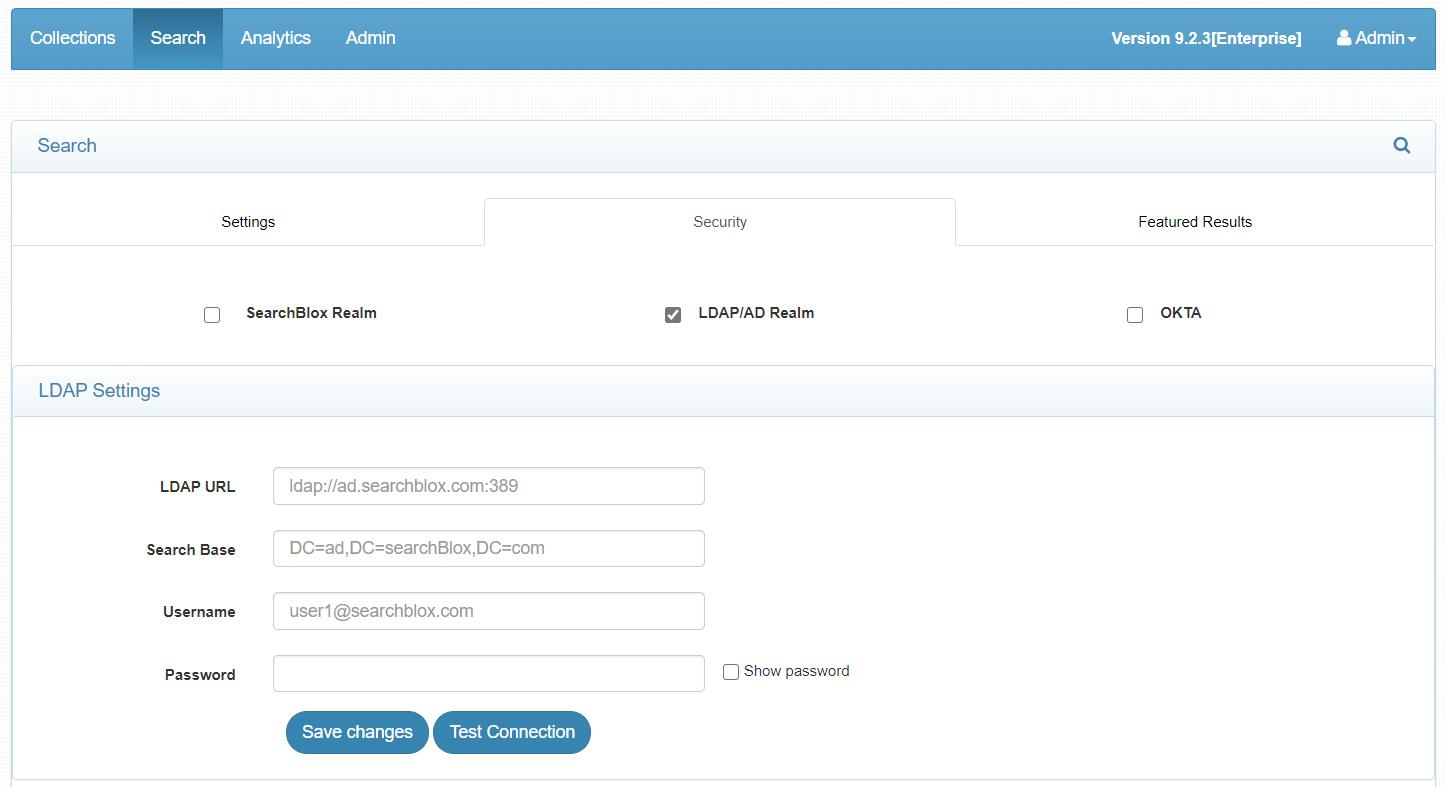
LDAP Settings
- Select LDAP/AD Realm
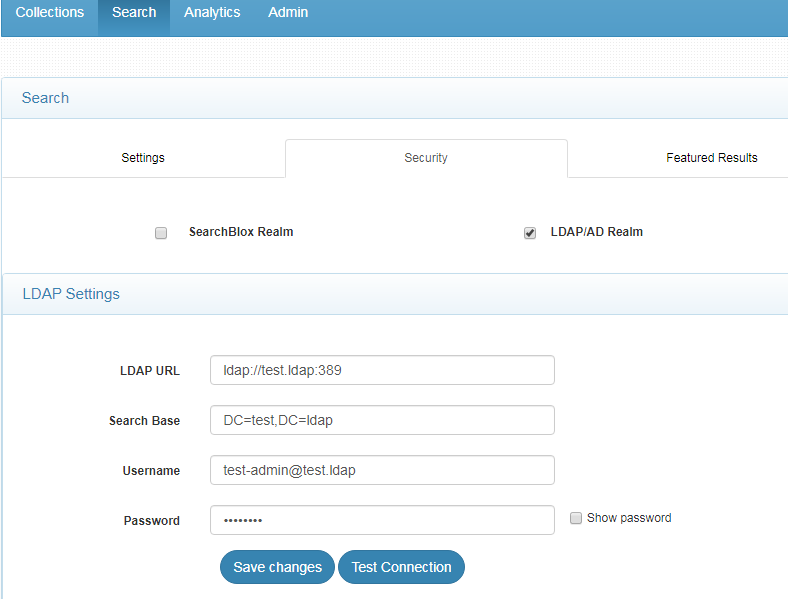
- Give the required LDAP details
| Field | Description |
|---|---|
| LDAP URL | LDAP URL that specifies a base search for the entries |
| Search Base | Search Base for the active directory |
| Username | Admin username |
| Password | Password for the username |
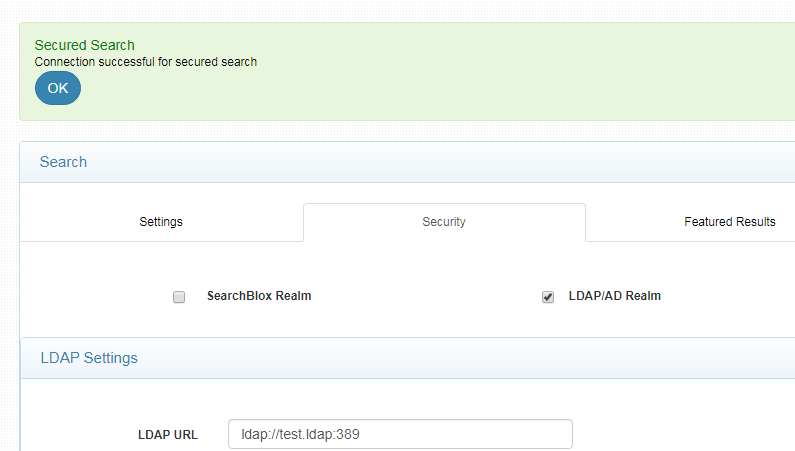
- Test the connection. For a successful connection you would get the message as shown:
Add Security Group
- Using this setting you can configure security group settings for LDAP/ Active Directory.
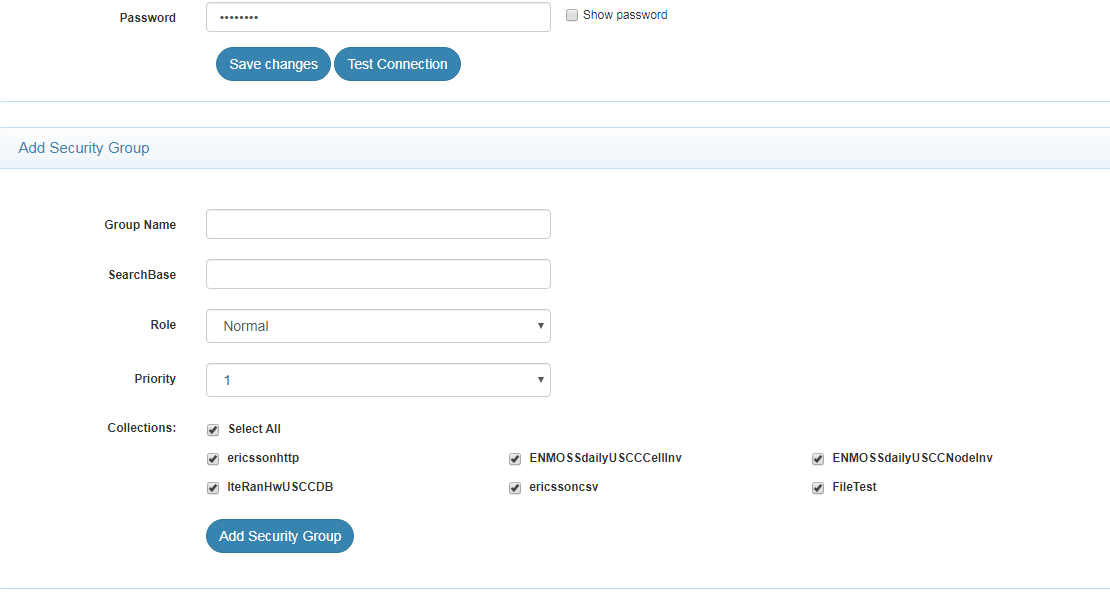
- Give the parameters for the Security Group for LDAP. The information on the parameters is provided in the following table
| Field | Description |
|---|---|
| Group Name | Name of the security group. This can be given by the user based on their OU or requirement. Group Name accepts alphanumeric characters of length min. 3 - max. 50 characters. The only special character allowed in Group Name is underscore. |
| Search Base | Search Base for the active directory/security group |
| Role | There are two values Normal or Sensitive. Default is Normal. Sensitive users have access to encrypted content Collection Encryption |
| Priority | The priority of the Group. Usecase: If a user is in two groups, the group which has a greater priority will be taken as the user group. |
| Collections | Collections accessible by the users in the Group |
- After adding the groups, you can view the same under Security User Groups dashboard as shown:
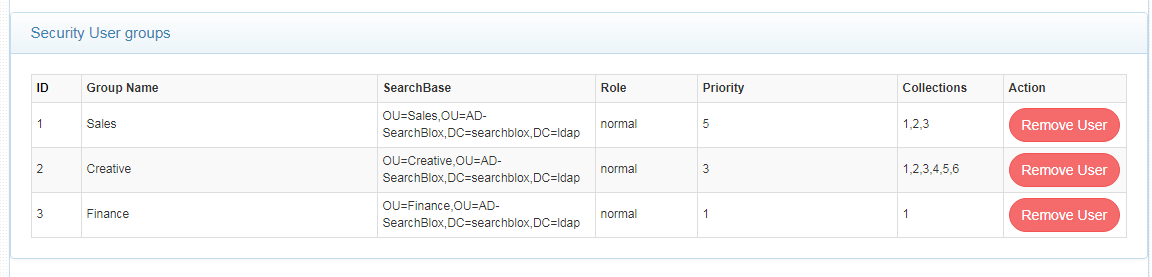
Features of Security Groups in LDAP Realm
Group Settings
- After providing the LDAP settings, it is mandatory to give Group settings. This is required to integrate collection based security with LDAP security for the search results.
- When creating a group, one can assign a set of collections to the same, then the user belonging to the group will have access only to the same set of collections.
- The users belonging to the OU, that is, Organizational Unit will belong to the group
- It is possible to create more than one group for one Organizational Unit (OU)
- The permissions and users for a group are fetched based on the search base provided, and therefore, it is an important parameter for Security User Group creation
Group Naming
- LDAP security groups can be named according to the Microsoft naming convention, allowing special characters.
- According to the Microsoft documentation, the LDAP distinguished name is globally unique. For example, the distinguished name of a computer named mycomputer in the MyOrganizationalUnit organizational unit in the microsoft.com domain is CN=mycomputer, OU=MyOrganizationalUnit, DC=microsoft, DC=com.
- For example, “A602-AC-DMASFS2_sdata RW”
Priority
- When a user is available in two groups, they will be considered in the group of higher priority.
For example,
Let us consider that the user belongs to group A with priority 5 and access to collection 1 and also belongs to group B with priority 3 and access to collection 2. Due to higher priority in group A, they will be considered to belong in Group A and therefore, will have access to results only for collection 1.
Sensitive User
- Only the users with a sensitive role would be able to view encrypted content. Please refer Collection Encryption for more details on Encryption.
Accessing Secure Search for LDAP Realm
Log in using LDAP/AD credentials here:
https://localhost:8443/searchblox/plugin/index.html
Then perform the secure search.
Updated over 4 years ago
What’s Next
